-

The Quantum Threat: Why Post-Quantum Cryptography is Our Best Defense for the Future
As quantum computing continues its steady march toward practicality, the digital infrastructure that secures our global communications, banking, military, and private data is under unprecedented threat. Quantum computers are not just another leap in processing power—they represent a fundamental shift that could render today’s encryption obsolete in a matter of minutes. Preparing for this…
-

Beyond Quantum: How Post-Quantum Cryptography is Securing the Future
🔐 With the rise of quantum computing, traditional encryption may soon become obsolete. But there’s already a new generation of cryptography designed to withstand even quantum threats—welcome to the era of Post-Quantum Cryptography (PQC). The Quantum Threat: Breaking the Unbreakable Today’s internet security relies heavily on classical encryption algorithms such as RSA, AES, and…
-
Quantum Internet vs. 5G: Comparing Safety and Health Risks of Emerging Technologies
As the world races toward a future powered by advanced connectivity, two revolutionary technologies are shaping the global communication infrastructure: 5G networks and the Quantum Internet. While both promise groundbreaking speed, security, and efficiency, concerns regarding their health and environmental impact—especially with 5G—have sparked widespread debate. This article explores the risks associated with 5G…
-

Post-Quantum Cryptography: Securing the Future in a Quantum World
As the capabilities of quantum computers rapidly advance, the security of classical cryptographic systems faces an unprecedented threat. Post-Quantum Cryptography (PQC) emerges as a vital frontier in the effort to safeguard digital communication, data, and infrastructure from quantum-enabled attacks. This article explores what post-quantum cryptography is, why it matters, how it works, and the…
-
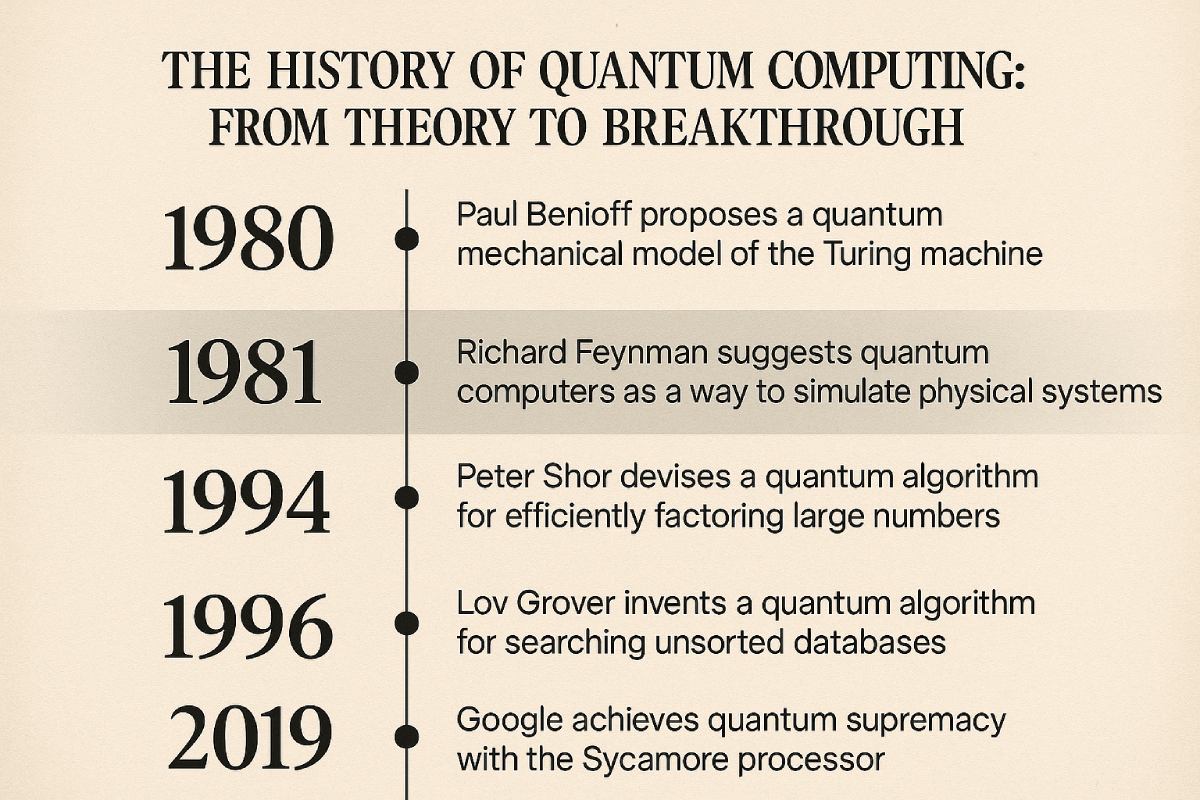
The History of Quantum Computing: From Theory to Breakthrough
Introduction Quantum computing, once a theoretical curiosity rooted in the strange laws of quantum mechanics, has evolved into one of the most promising frontiers in science and technology. Unlike classical computers that process information in bits (0s and 1s), quantum computers use qubits—quantum bits that leverage superposition and entanglement to perform complex computations exponentially…