-
Quantum Internet vs. Classical Internet: Unveiling the Next Leap in Connectivity
As we stand on the edge of a new technological frontier, the rise of quantum technologies promises to reshape every layer of the digital infrastructure we rely on today. One of the most revolutionary concepts emerging from this space is the Quantum Internet — a secure, ultra-fast network that leverages the laws of quantum…
-

5G vs Quantum Internet: The Next Leap in Connectivity
As the world embraces the transformative power of 5G, a new frontier in connectivity is quietly emerging quantum internet. While 5G is designed to deliver ultra-fast speeds, low latency, and high device capacity, quantum internet promises a paradigm shift in how information is transmitted, secured, and processed. But how do these two technologies truly…
-
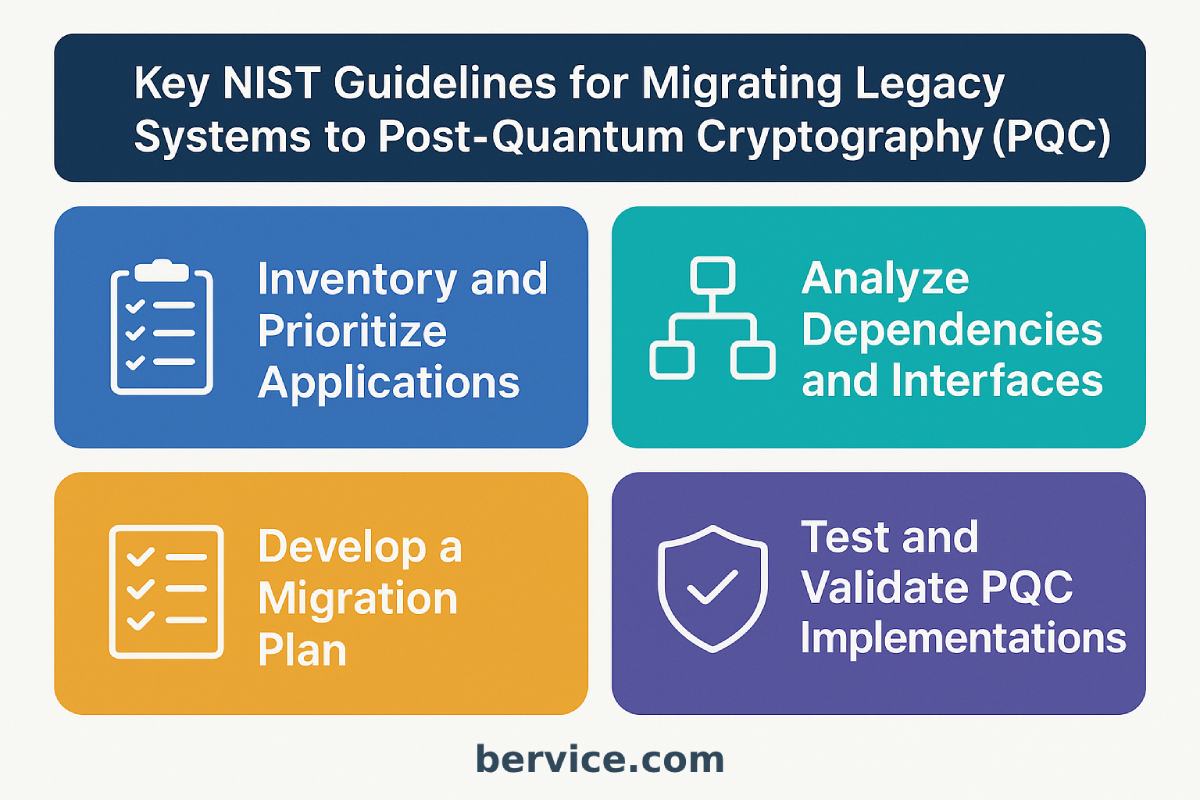
Key NIST Guidelines for Migrating Legacy Systems to Post-Quantum Cryptography (PQC)
As the advent of quantum computing threatens the foundations of traditional cryptographic systems, organizations across the globe are being urged to transition toward Post-Quantum Cryptography (PQC). To guide this critical migration, the National Institute of Standards and Technology (NIST) has played a central role by issuing standards, recommendations, and timelines that help industries and…
-

What is NIST and Its Role in Post-Quantum Cryptography (PQC)?
Introduction: Understanding NIST’s Global Importance The National Institute of Standards and Technology (NIST) is a U.S. federal agency under the Department of Commerce, dedicated to advancing measurement science, standards, and technology. Since its founding in 1901, NIST has played a central role in developing frameworks and standards used across industries—from cybersecurity and cryptography to…
-
First Steps Toward Post-Quantum Security in AWS Infrastructure
As quantum computing continues to evolve, it presents both unprecedented computational power and significant cybersecurity threats. Classical encryption algorithms such as RSA, ECC, and DH—widely used in modern cloud infrastructure—are vulnerable to attacks from sufficiently powerful quantum computers using Shor’s algorithm. To future-proof sensitive data and maintain customer trust, organizations using AWS must begin…