-

AGI by 2030: What It Is—and How It Could Reshape the Global Macro Economy
Executive summary (no sugarcoating) 1) What do we mean by AGI? Operational definition: a system that can (a) learn any cognitive task humans can, (b) transfer that learning across domains with minimal prompting, and (c) reliably achieve human-level outcomes in real-world workflows.Practical 2030 reality: Firms won’t wait for textbook AGI. Near-AGI models that can…
-

File & Password Vault with Zero-Knowledge Proof: Proving Ownership Without Exposing Secrets
In the modern digital landscape, trust is a liability. Every time users share sensitive data to “prove” ownership, they open the door to risk — data leaks, surveillance, insider threats, and future exploitation. The traditional security model assumes “trust and verify.” But the world has changed. The next wave of security infrastructure is “don’t…
-

Data Immortality and the Philosophy of Digital Ownership
1. A New Age of Data: The Birth of Digital Immortality Every moment we live, we generate data — from financial transactions and health records to conversations and creative works. This ever-growing digital footprint outlives us, shaping how societies, governments, and corporations understand and influence the world. The concept of Data Immortality refers to…
-

Post-Quantum Security: How Bervice Redefines Data Protection for the Quantum Era
Introduction: The Quantum Threat to Today’s Encryption For decades, digital security has relied on mathematical problems so complex that even the fastest classical computers struggle to solve them. But quantum computing changes everything. Algorithms like Shor’s and Grover’s can, in theory, break RSA, ECC, and other public-key systems that form the backbone of modern…
-
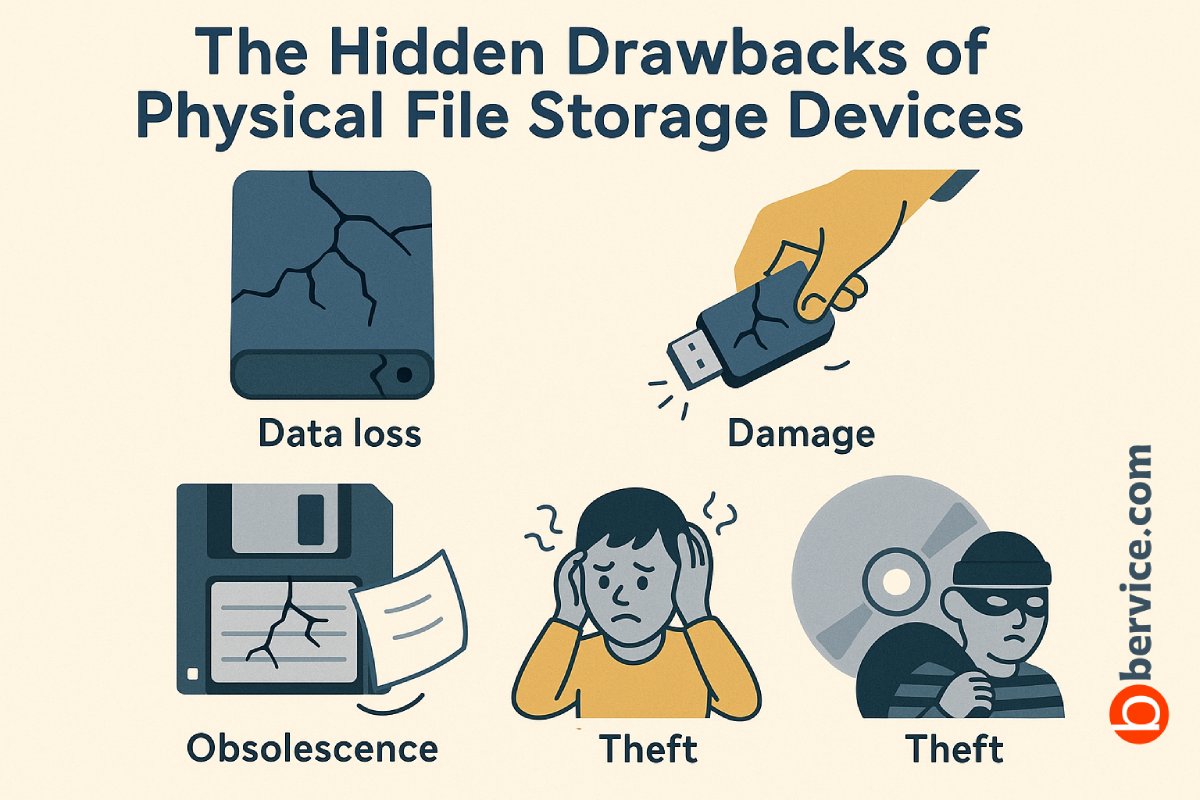
The Hidden Drawbacks of Physical File Storage Devices
While flash drives, external hard disks, and other physical file storage devices have long served as reliable companions for data backup and transfer, they come with significant limitations in today’s fast-evolving digital landscape. Despite their convenience and portability, these hardware-based solutions present challenges in security, durability, scalability, and sustainability that make them increasingly obsolete…