-

Quantum Vulnerabilities in Modern Cryptography
A Historical Perspective and a Forward-Looking Defense Strategy Introduction A Threat That Arrives Late but Strikes Early Quantum computing does not yet pose an operational threat to today’s cryptographic systems. No publicly known quantum computer can currently break RSA, ECC, or other widely deployed public-key schemes at meaningful scales.However, this apparent safety is deceptive.…
-

Malvertising How Cybercriminals Exploit Trust to Steal User Data
In recent years, cybercriminals have significantly refined their tactics to deceive users. Rather than relying on crude scams or obvious malware, attackers now invest time and resources into analyzing emerging technologies, user behavior, and legitimate digital ecosystems. Their goal is simple but dangerous: blend malicious activity seamlessly into everyday online experiences. According to a…
-
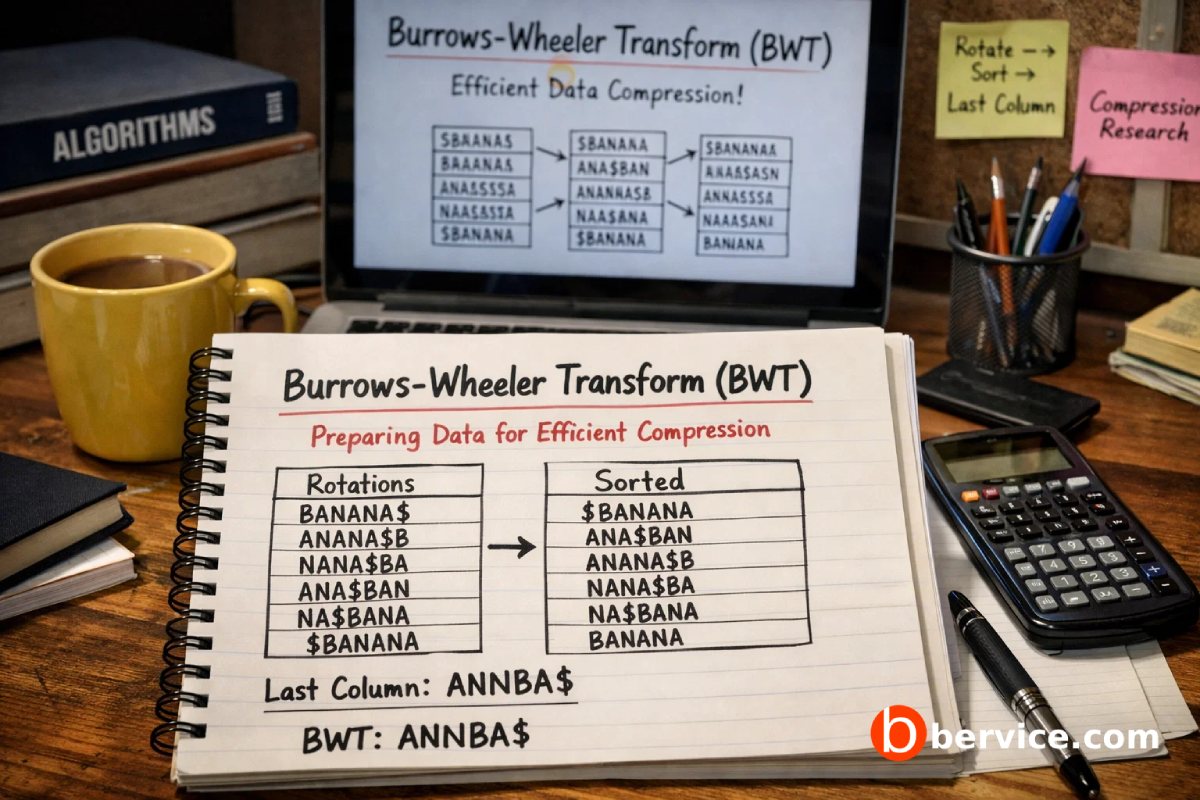
Burrows Wheeler Transform BWT Preparing Data for Efficient Compression
Introduction Data compression is not only about reducing file size it is about transforming data into a form that can be encoded more efficiently. One of the most elegant examples of this idea is the Burrows–Wheeler Transform (BWT). Unlike traditional compression algorithms that directly reduce data size, BWT is a reversible data transformation that…
-

Quantum Data Compression Trading with Reality in an Irreversible Future
Introduction: Compression Beyond Classical Intuition In classical computing, data compression is a reversible engineering problem. Information is encoded redundantly, statistical patterns are exploited, and within theoretical limits such as Shannon entropy data can be compressed and later reconstructed with perfect or near-perfect fidelity. Quantum computing breaks this intuition entirely. Quantum data compression is not…
-

P4 Programming Protocol-Independent Packet Processors
Building Programmable Networks Directly in Hardware Introduction Modern networks are no longer just passive packet-forwarding fabrics. They are expected to enforce security policies, perform real-time telemetry, mitigate attacks, and adapt dynamically to application needs. Traditional network devices, however, rely on fixed-function data planes, where packet parsing and processing logic is hard-coded into ASICs. This…