-

Blockchain-Powered Quality Assurance: Unlocking Trust and Transparency in Modern Supply Chains
In an era where consumer expectations are rising and regulatory standards are tightening, Quality Assurance (QA) has become a mission-critical process across industries. However, traditional QA methods often suffer from issues such as lack of transparency, data manipulation, manual errors, and difficulty in tracing accountability. Blockchain technology, known for its decentralized, tamper-proof nature, is…
-

2026: The Year of Infrastructure Transition and Post-Quantum Cryptography (PQC) Security
As the horizon of quantum computing draws nearer, the year 2026 marks a pivotal moment in the cybersecurity and digital infrastructure landscape. Global enterprises, governments, and tech platforms are no longer just theorizing about quantum threats — they are actively transitioning their infrastructure to prepare for the post-quantum era. Post-Quantum Cryptography (PQC) is no…
-

Securing Web2 Infrastructure Against Quantum Computer Threats
The Strategic Benefits of Adopting Post-Quantum Cryptography (PQC) Introduction: the looming “Q-Day.”Quantum computers are progressing toward the point where they can factor large integers and solve discrete-log problems fast enough to break today’s RSA and ECC keys in minutes. Industry observers now place practical quantum attacks inside the current decade—Google’s Quantum AI group even…
-
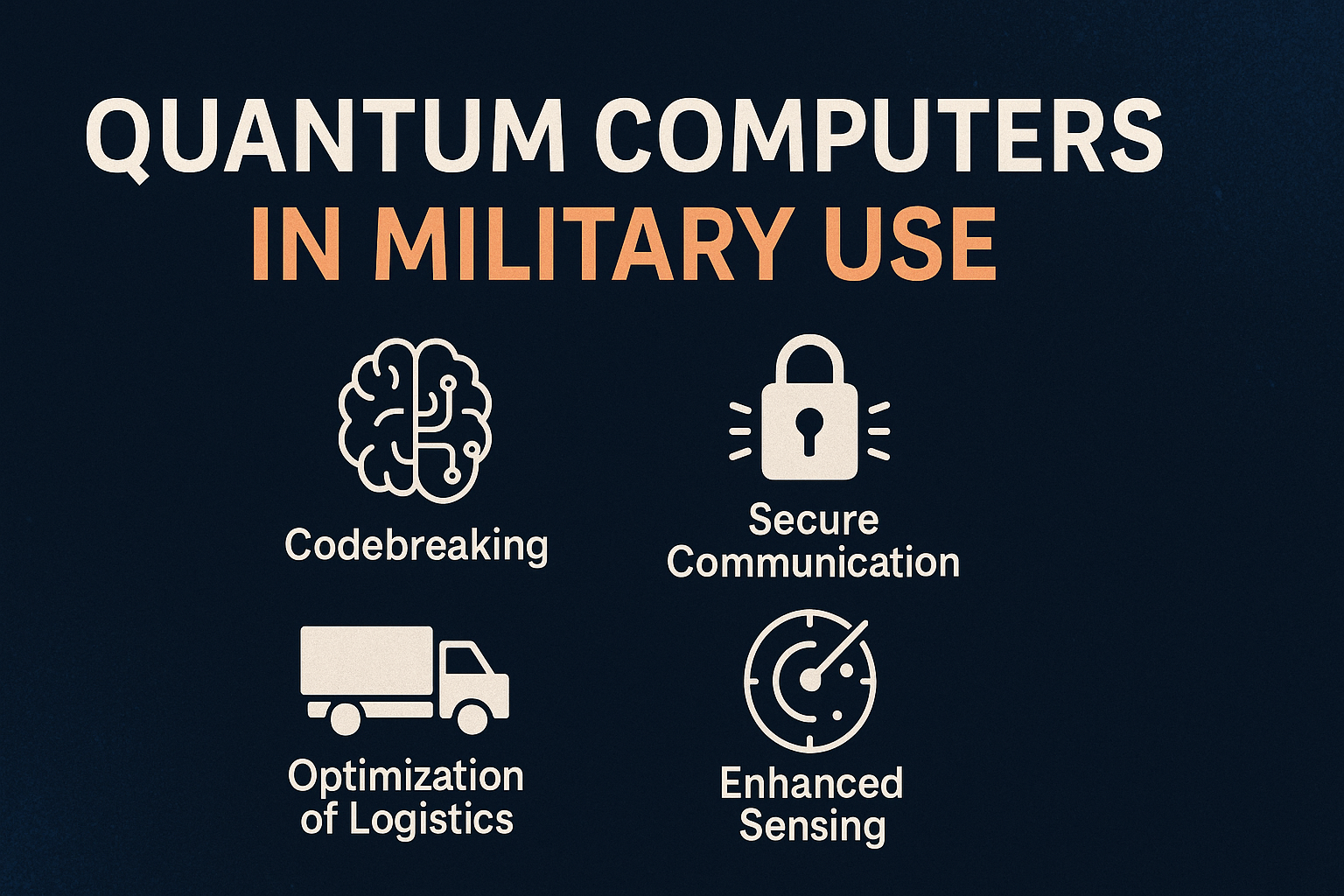
Quantum Computers in Military Applications: Revolutionizing Defense Technology
Quantum computing, once a theoretical curiosity, is now on the brink of revolutionizing multiple sectors — none more critically than the military. As nations race toward technological superiority, defense organizations are exploring how quantum capabilities can redefine strategic operations, cybersecurity, and advanced weapon systems. This article explores the transformative impact of quantum computers in…
-
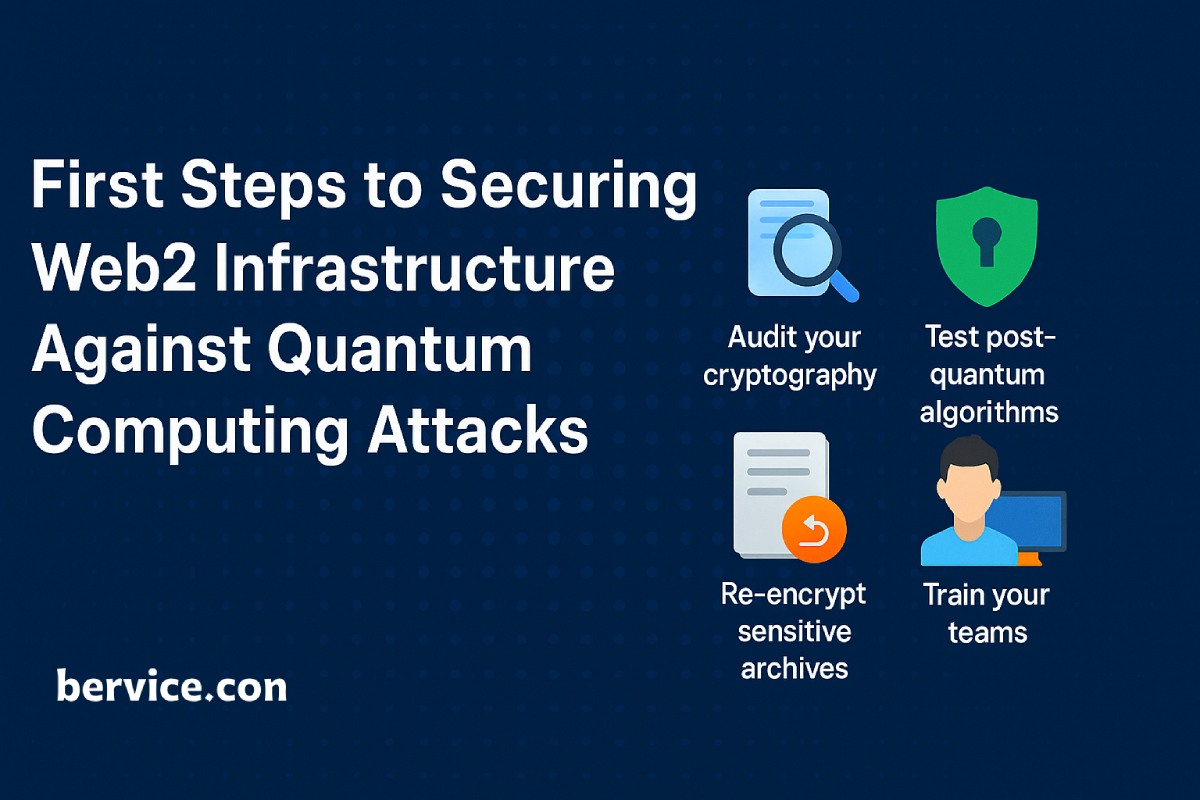
First Steps to Securing Web2 Infrastructure Against Quantum Computing Attacks
As the era of quantum computing approaches, organizations relying on traditional Web2 infrastructures face a looming threat: quantum attacks capable of breaking today’s cryptographic systems. Unlike classical computers, quantum machines leverage quantum mechanics to solve certain problems exponentially faster — a capability that directly undermines the foundations of modern cybersecurity, especially public-key cryptography. In…