-

Data Immortality and the Philosophy of Digital Ownership
1. A New Age of Data: The Birth of Digital Immortality Every moment we live, we generate data — from financial transactions and health records to conversations and creative works. This ever-growing digital footprint outlives us, shaping how societies, governments, and corporations understand and influence the world. The concept of Data Immortality refers to…
-

Post-Quantum Security: How Bervice Redefines Data Protection for the Quantum Era
Introduction: The Quantum Threat to Today’s Encryption For decades, digital security has relied on mathematical problems so complex that even the fastest classical computers struggle to solve them. But quantum computing changes everything. Algorithms like Shor’s and Grover’s can, in theory, break RSA, ECC, and other public-key systems that form the backbone of modern…
-
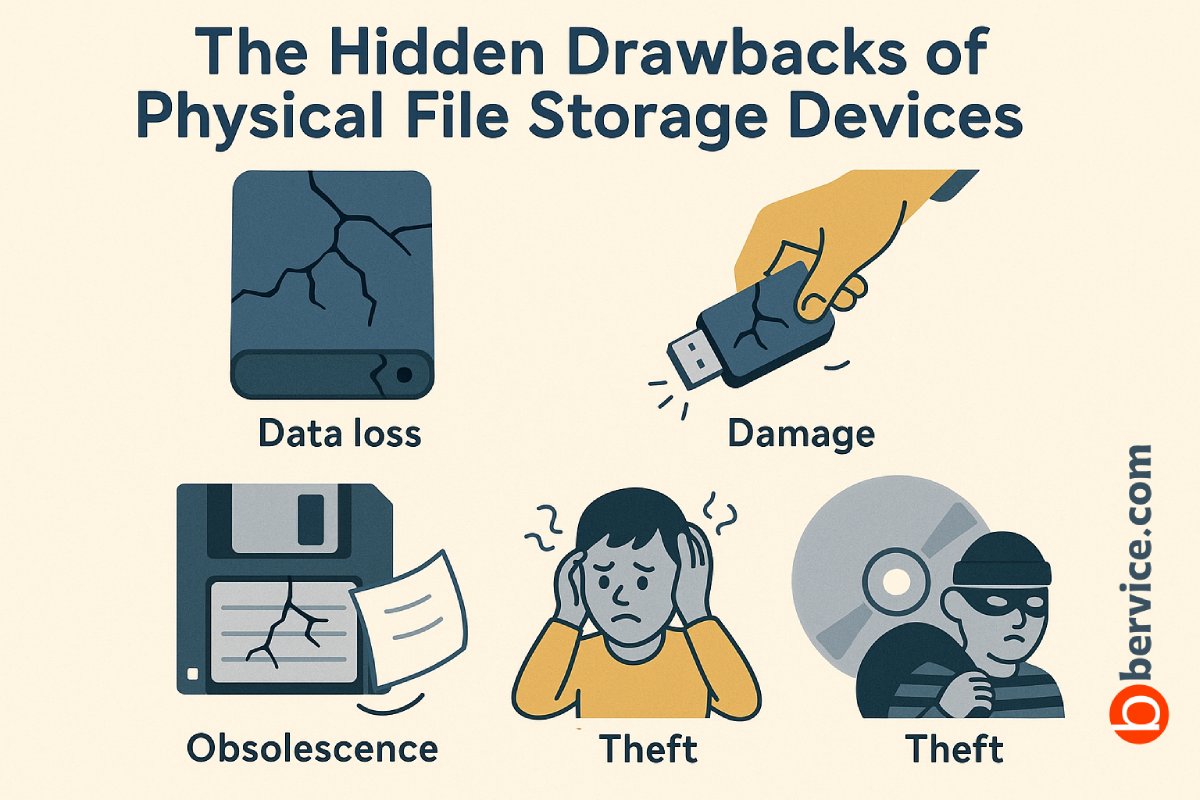
The Hidden Drawbacks of Physical File Storage Devices
While flash drives, external hard disks, and other physical file storage devices have long served as reliable companions for data backup and transfer, they come with significant limitations in today’s fast-evolving digital landscape. Despite their convenience and portability, these hardware-based solutions present challenges in security, durability, scalability, and sustainability that make them increasingly obsolete…
-

The Role of NIST in Security: Mission, Goals, and Global Impact
Introduction The National Institute of Standards and Technology (NIST) is a U.S. federal agency under the Department of Commerce, founded in 1901. Its original mission was to promote innovation, industrial competitiveness, and technological progress by creating measurement standards. Over time, as digital technologies and cyber threats became central to modern life, NIST took on…
-
Data Immortality: How Your Information Can Live Forever
In the digital era, the loss of data has become one of the greatest fears for individuals and organizations alike. Hard drives fail, companies collapse, and servers are wiped clean by accidents or malicious attacks. But what if data could achieve a form of immortality living on independently of any single provider, company, or…