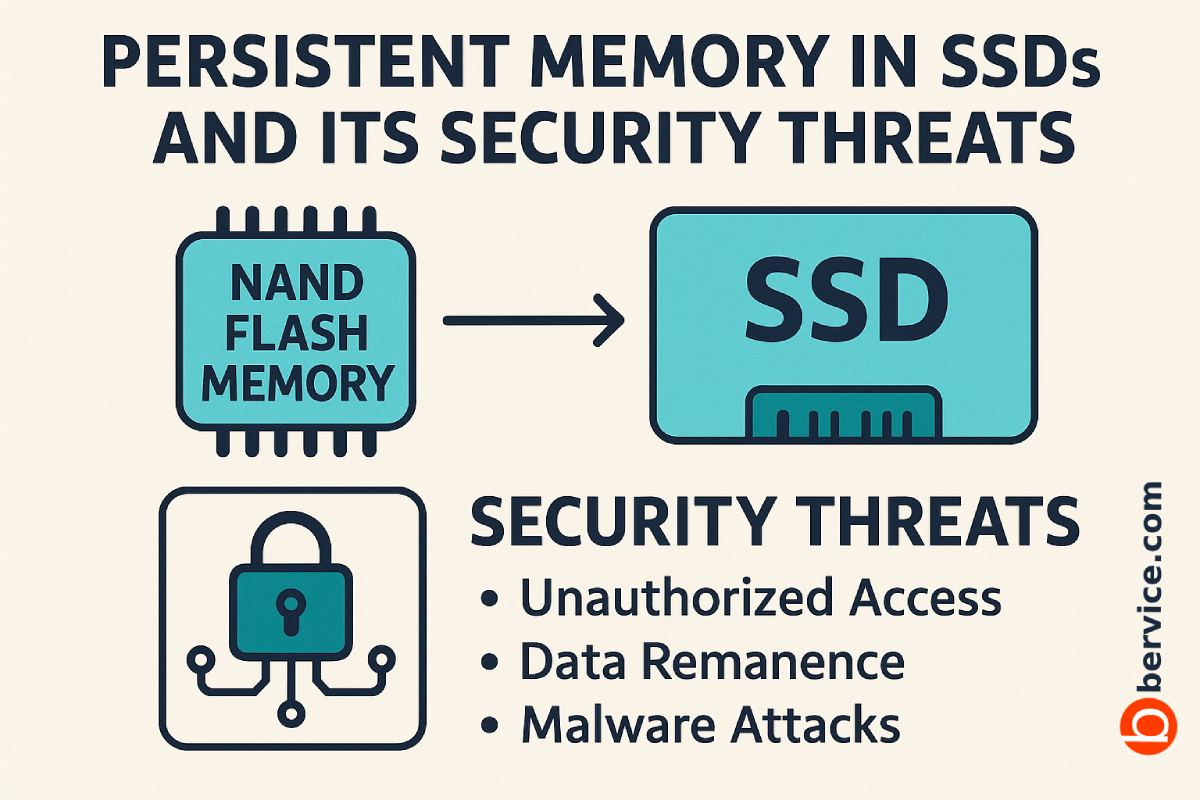
1. Introduction: The Rise of Persistent Memory
In recent years, persistent memory technologies have blurred the line between traditional storage and volatile memory. Unlike conventional DRAM, persistent memory retains data even after power is removed, combining low latency, high throughput, and non-volatility. Modern solid-state drives (SSDs) increasingly integrate persistent buffers and caches to improve performance and endurance.
While this advancement accelerates system efficiency, it also opens up new attack surfaces that traditional storage security models fail to address. The fact that data can survive power cycles introduces risks that go beyond ordinary disk encryption and standard data sanitization procedures.
2. How Persistent Memory Works in SSDs
Most enterprise and consumer SSDs employ multiple layers of memory:
- NAND Flash Storage: The primary non-volatile medium where bulk data is stored.
- DRAM Cache: A volatile cache used for fast mapping table access.
- Persistent Cache (e.g., NVRAM, PCM, MRAM): Used to store data temporarily with non-volatile retention.
When a write request occurs, data may first land in the persistent buffer before being flushed to NAND. This buffering improves write performance and reduces latency, but it also means critical data can remain in the device for extended periods, even when the drive is “powered off.”
3. Security Threats from Persistent Memory
3.1 Data Remanence and Forensic Recovery
Persistent caches can retain sensitive information such as encryption keys, user data, or metadata. Unlike DRAM, which loses data quickly after power-off, NVRAM and other persistent elements retain data for minutes, hours, or even indefinitely.
Attackers with physical access can extract residual data through chip-off or cold-boot-like techniques, bypassing OS-level security.
3.2 Bypass of Secure Erase Mechanisms
Most secure erase commands target the NAND storage layer. If sensitive data remains in the persistent buffer and isn’t properly flushed or sanitized, data can survive secure erasure, leaving organizations with a dangerous blind spot in their data sanitization policy.
3.3 Firmware Exploitation
Persistent memory regions are often managed by the SSD’s internal controller firmware. Exploiting vulnerabilities in this firmware can give an attacker low-level access to cached sensitive data. In some cases, malicious firmware can re-inject previously cached data into the system after reboot, enabling stealthy persistence.
3.4 Supply Chain and Implant Risks
Advanced threat actors can use persistent memory as a covert implant location. Because the cache sits below the OS and hypervisor layers, implants stored there may survive reinstallation of operating systems or even drive reformatting, creating a hidden persistence layer.
4. Attack Scenarios
- Scenario A: An attacker steals a decommissioned SSD from a data center and recovers previously buffered plaintext database fragments from persistent memory.
- Scenario B: A malicious insider exploits firmware vulnerabilities to exfiltrate keys stored temporarily in persistent cache.
- Scenario C: A sophisticated APT implants malware into SSD firmware that leverages persistent memory to reappear after system wipes.
These are not theoretical — similar low-level firmware exploits have been observed in real-world attacks against BIOS, UEFI, and hardware controllers.
5. Defensive Measures and Best Practices
5.1 Hardware-Level Encryption
Always use SSDs with hardware-based encryption that extends protection to all memory layers, including persistent buffers. AES-256 or stronger encryption, tied to a secure key management system, can significantly reduce exposure.
5.2 Secure Sanitization Protocols
Traditional “secure erase” may not be enough. Organizations should use crypto-erase (key destruction) or enhanced secure erase commands that explicitly clear persistent caches. Verification and post-sanitization testing are essential.
5.3 Firmware Integrity and Updates
Implement strict firmware signing and attestation policies. Ensure SSD firmware updates are authenticated and monitored for tampering. Use trusted supply chains to reduce implant risks.
5.4 Physical Security and Disposal Procedures
When devices are decommissioned, physical destruction or certified secure wiping of persistent memory components should be performed. Logical erase alone is insufficient when dealing with NVRAM or MRAM-based caches.
5.5 System Architecture Hardening
Employ full disk encryption, secure boot, and measured boot to minimize the attack surface. Isolate sensitive workloads on hardware that supports trusted execution and verified storage paths.
6. Future Outlook: Persistent Memory Security by Design
As persistent memory technologies evolve — especially with the rise of CXL-based memory expansion and hybrid SSD architectures — security must be designed into the hardware layer itself. Future drives should provide auditable sanitization logs, built-in zeroization mechanisms, and tamper-evident memory modules.
Regulatory bodies and data protection frameworks are also expected to update standards around persistent memory handling, pushing for stronger guarantees in both enterprise and consumer storage markets.
7. Conclusion
Persistent memory in SSDs represents both a breakthrough in performance and a critical security risk if not managed properly. It fundamentally alters how data persists across power states and how attackers can exploit low-level device behavior.
Organizations must rethink their storage security policies, integrate persistent memory into their threat models, and adopt layered defenses that cover not just data at rest, but data in transition inside the device.
In the race between storage innovation and cybersecurity, ignoring persistent memory is not an option.
Connect with us : https://linktr.ee/bervice